
KernSafe iStorage Server as first software fully supports Itanium architecture for creating iSCSI SAN Targets.
The Itanium architecture is based on explicit instruction-level parallelism, in which decisions about which instructions to execute in parallel must be made by the compiler. This contrasts with other superscalar architectures which depend upon processor functionality that keeps track of instruction dependencies at runtime. Itanium cores up to and including Tukwila execute up to six instructions per clock cycle.
Main benefits of Itanium architecture are:
- Multi-OS support
- Lower overall Cost of Ownership for enterprise IT
- ·Assurance of leading performance and scalability over the long-term
- Greater memory addressability
- More complex applications and computing environments
- Secure web server transactions
- Computer aided design such as Mechanical Analysis
- Very large memory databases
- Industry-standard servers in every tier of the data center
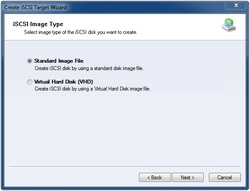
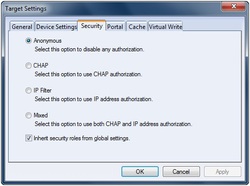
iStorage Server is an IP SAN solution that allows you quickly export existing storages such disk images, physical disks, partitions, CD/DVD-ROMs, tapes or any other type of SCSI based devices and even a variety of popular CD/DVD images to its client machines, which delivers immediate benefits allowing storage to be consolidated, virtualized and centrally managed. iStorage Server also provides RAID-1 (mirror) feature, which allows you create two devices for mirror backup, the mirror devices can be local image files or remote iSCSI devices. iStorage Server has been added support for Microsoft Virtual Disk File (VHD) and VHD snapshots at the recent release. So it is an ideal choice for any sized business.



 RSS Feed
RSS Feed