 In iStorage Server you can create a Security Images for every Client Machine. Thanks to this option every employee can have its own private encrypted space where he/she can store important data that can’t be accessed by anyone else.
You can create such image using iStorage Server in just few steps:
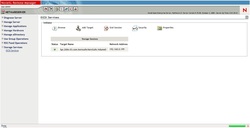
1. Open iStorage Server Management Console. 2. Click Create button to create a new target.
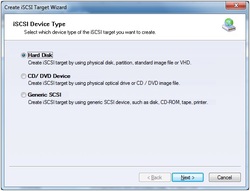
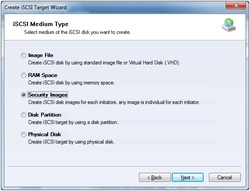
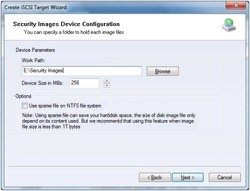
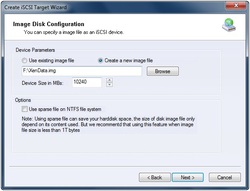
3. Chose creation of Hard Disk. 4. Choose Security Images to create an encrypted image. 5. Select where to save the file as well as the size of it. Checking option Use sparse file on NTFS file system can help you save disk space but it is not recommended to use on when the image file is bigger than 1T bytes.
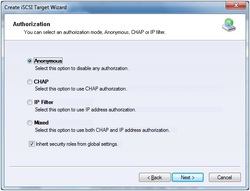
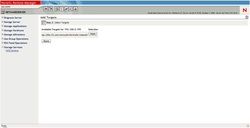
6. Choose the Authentication Mechanism.
o All initiators will get full access permission without any authorization required. - CHAP (Challenge-handshake authentication protocol)
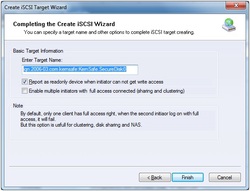
o All initiators need to specify a CHAP user and secret to connect to the target. iStorage Server has a built-in user called “Guest”, which is used for initiators without CHAP secret specified. o All initiators will be authorized by the incoming IP address defined by IP Filter roles. o Security policy is determined by both CHAP and IP Filters. If you check Inherit security roles from global settings, all client security roles are form global settings, otherwise, each client will have its own permission. 7. Choose name for your Security Image file. If you check Report as readonly device when initiator cannot get write access, the system will give you a report when you load the target without write access.
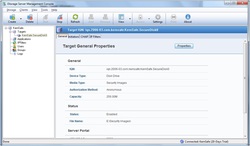
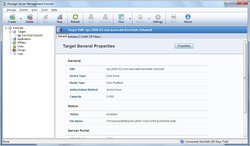
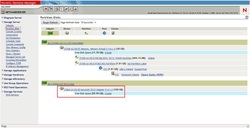
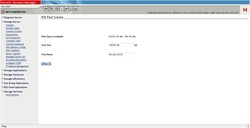
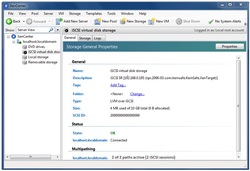
After creating the image, you can check information about it in the General Tab.
Connecting to the Security Image is even easier:
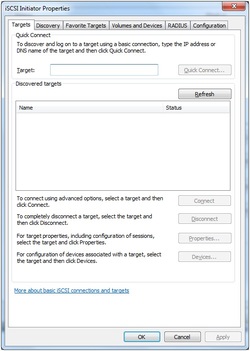
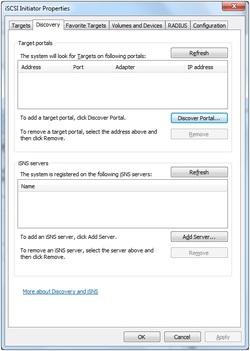
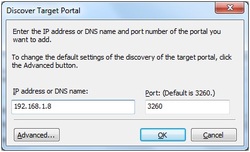
1. Open iSCSI Initiator. 2. Select the Discovery tab page. 3. Press the Discover Portal… button, the Discover Target Portal dialog will appear. Type the IP address and Port of your server. Default port is 3260.
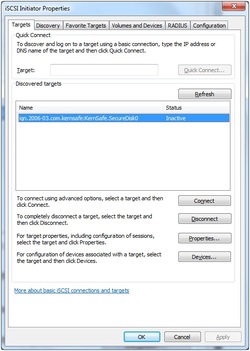
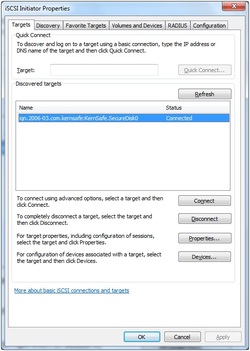
4. Change to Targets tab. Select the target in the Targets list, and then press the Connect button.
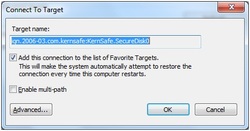
Then the Connect to Target dialog will appear. If your iSCSI target is using IP filter or Anonymous authorization, just press the OK button to continue.
Check Add this connection to the list of Favorite Targets, to log-on this target automatically after system boots.
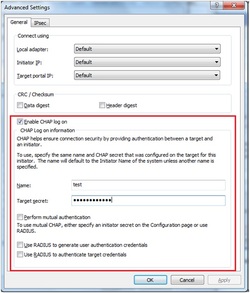
If your iSCSI target is using CHAP user authorization, press the Advanced… button, the Advanced Settings dialog will appear.
Select Enable CHAP log on and type Name and Target secret.
Now you are successfully connected to the iSCSI target.
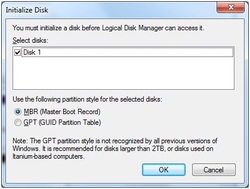
Open Disk Management (Right click on to Computer, click Manage, from the tree list on the left side choose Disk Management). An Initialize Disk window will appear.
6. After clicking OK, you can format your new Security Image and use it as if normal hard drive.
You can download Trial version of iStorage Server here.
 iStorage Server supports iSCSI SAN for Novell NetWare operating system iSCSI, an Internet Protocol (IP)-based storage networking standard for linking data storage facilities. By carrying SCSI commands over IP networks, iSCSI is used to facilitate data transfers over intranets and to manage storage over long distances. iSCSI can be used to transmit data over local area networks (LANs), wide area networks (WANs), or the Internet and can enable location-independent data storage and retrieval. It is a popular Storage Area Network (SAN) protocol, allowing organizations to consolidate storage into data center storage arrays while providing hosts (such as database and web servers) with the illusion of locally-attached disks. Unlike traditional Fibre Channel, which requires special-purpose cabling, iSCSI can be run over long distances using existing network infrastructure. Main benefits of using iSCSI SAN are: - iSCSI can be run over long distances using existing network infrastructure.
- Simplified and consolidated storage management
- Easier virtualization
- Low-cost hardware requirements
- Scalability and flexibility
- Reduced SAN management training requirements
- Ability to create a SAN from existing direct-attached storage servers
NetWare is a network operating system developed by Novell, Inc. It initially used cooperative multitasking to run various services on a personal computer, with network protocols based on the archetypal Xerox Network Systems stack. NetWare iSCSI includes several important features to help you create and manage a low-cost NetWare SAN: - Support for standard TCP/IP networks using commodity Ethernet hardware.
- Single point of administration through the browser-based NetWare Remote Manager. This lets you remotely manage your iSCSI SAN.
- Support for the iSCSI draft specification (Ratified Standard Draft 20).
- Support for Challenge Handshake Authentication Protocol (CHAP) authentication for initiator identity verification.
- Interoperability with industry standard iSCSI storage servers or targets, including Cisco, Network Appliance, Adaptec and others.
- Easy installation and configuration, especially compared to the complexity involved in installing and configuring a fibre channel SAN.
Combing iStorage Server with Novell NetWare will expand the application scope of your Novell NetWare server and workstation, thereby enabling WINDOWS server to expand the storage of your Novell NetWare computer. It also allows you to directly use the storage devices of the existing Windows server for Novell NetWare Server. With IP SAN solution provided by iStorage Server, you may install application and server software, as well as store data required wish you like.
Connecting to the iSCSI target created in iStorage Server is really simple under Novel Remote Manager. Just follow those steps:
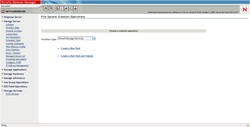
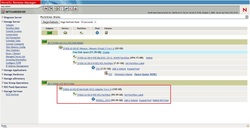
1. Open Novell Remote Manager and click on the iSCSI Services. Click on the Add Target button.
2. Type Network Address, of target the iSCSI. 3. Chose which target you want to add. 4. Confirm selection of your target.
5. Your target is successfully added. 6. From collapse tree menu, click Manage Server and choose Partition Disks. You will see an iSCSI you just added. To create a new partition click Create.
7. Chose partition type. Then click on Create a New Pool or Create a New Pool and Volume.
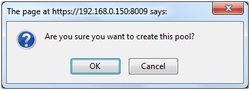
8. Specify the Pool Size and Pool Name. Click CREATE.
When a window will appear click on OK button to finalize creation of new NSS Pool.
Now, your target device is fully configured and ready to use.
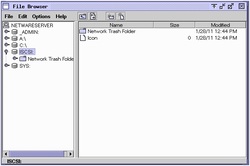
You can browse easily through the drive now using systems File Browser.
You can download Trial version of iStorage Server here.
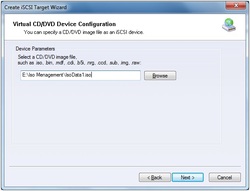
 iStorage Server supports centralized management using ISO files
KernSafe iStorage Server is an advanced and powerful, full-featured iSCSI Target software that makes any x86, x64 or even Itanium Windows machine into an iSCSI Target.
iStorage Server is an IP SAN solution that allows you quickly export existing storages such disk images, physical disks, partitions, CD/DVD-ROMs, tapes or any other type of SCSI based devices and even a variety of popular CD/DVD images to its client machines, which delivers immediate benefits allowing storage to be consolidated, virtualized and centrally managed. iStorage Server also provides RAID-1 (mirror) feature, which allows you create two devices for mirror backup, the mirror devices can be local image files or remote iSCSI devices. iStorage Server has been added support for Microsoft Virtual Disk File (VHD) and VHD snapshots at the recent release. So it is an ideal choice for any sized business.
Thanks to iStorage Server you can create a large number of iSCSI targets which actually are ISO files. After creating an iSCSI target a user can connect to it using iSCSI Initiator to log in to the target and use it as a virtual CD/DVD ROM.
This solution can help you create centralized management. A centralized management infrastructure enables you to create and manage server far more efficiently than a local management implementation.
You can store all of your ISO files on to one server, and create iSCSI Targets for other users to create onto them. This will save you time and money because it is easier to manage one server then several of them.
iStorage Server is available for Trial Download here.
 iStorage Server helps share data between workstation and lapboard
KernSafe iStorage Server is an advanced and powerful, full-featured iSCSI Target software that makes any x86, x64 or even Itanium Windows machine into an iSCSI Target.
iStorage Server is an IP SAN solution that allows you quickly export existing storages such disk images, physical disks, partitions, CD/DVD-ROMs, tapes or any other type of SCSI based devices and even a variety of popular CD/DVD images to its client machines, which delivers immediate benefits allowing storage to be consolidated, virtualized and centrally managed. iStorage Server also provides RAID-1 (mirror) feature, which allows you create two devices for mirror backup, the mirror devices can be local image files or remote iSCSI devices. iStorage Server has been added support for Microsoft Virtual Disk File (VHD) and VHD snapshots at the recent release. So it is an ideal choice for any sized business.
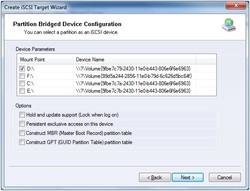
Using KernSafe iStorage Server you can easily share data between workstation and lapboard. You can do it by simply exporting a partition or a whole hard drive in the iStorage Server. You can even chose if you want to share in virtual write mode or in read only mode.
This solution is ideal when you want to securely share some data between computers using existing LAN network or Internet. iServer supports CHAP user authorization as well as IP Filter. You can even combine those two security methods into Mixed one.
You can download Trial version of iStorage Server here.
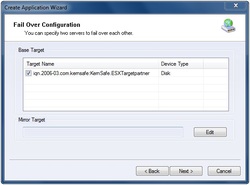
 iStorage Server supports creating a High-Availability iSCSI SAN for VMware ESX and VMware ESXi VMware ESX and VMware ESXi are “bare-metal” hypervisors, meaning they install directly on top of the physical server and partition it into multiple virtual machines that can run simultaneously, sharing the physical resources of the underlying server. Each virtual machine represents a complete system, with processors, memory, networking, storage and BIOS, and can run an unmodified operating system and applications. Combing iStorage Server with VMware ESX Server will expand the application scope of your virtual server, thereby enabling WINDOWS server to expand the storage of your virtualized server. It also allows you to directly use the storage devices of the existing Windows server for VMware ESX Server. With IP SAN solution provided by iStorage Server, you may set up operating system, install application and server software, as well as store data required by your virtual machines. High availability is the implementation of technology so that if a component fails, another can take over for it. By using highly available platforms, the downtime for a system can be reduced, and, in many cases, it can be reduced to a short enough time that the users of the system do not see the failure. If you want to learn more about iStorage Server HA iSCSI SAN technology for VMWare ESX / ESXi Server, and how to use it, please refer to this White Paper.
You can download Trial version of iStorage Server here.
 iStorage Server supports iSCSI SAN for Linux operating systems iSCSI, an Internet Protocol (IP)-based storage networking standard for linking data storage facilities. By carrying SCSI commands over IP networks, iSCSI is used to facilitate data transfers over intranets and to manage storage over long distances. iSCSI can be used to transmit data over local area networks (LANs), wide area networks (WANs), or the Internet and can enable location-independent data storage and retrieval. It is a popular Storage Area Network (SAN) protocol, allowing organizations to consolidate storage into data center storage arrays while providing hosts (such as database and web servers) with the illusion of locally-attached disks. Unlike traditional Fibre Channel, which requires special-purpose cabling, iSCSI can be run over long distances using existing network infrastructure. Main benefits of using iSCSI SAN are: - iSCSI can be run over long distances using existing network infrastructure.
- Simplified and consolidated storage management
- Easier virtualization
Linux is one of the most prominent examples of free and open source software collaboration, typically all the underlying source code can be used, freely modified, and redistributed, both commercially and non-commercially, by anyone under licenses such as the GNU General Public License. Typically Linux is packaged in a format known as a Linux distribution for desktop and server use. Combing iStorage Server with Linux will expand the application scope of your Linux server and workstation, thereby enabling WINDOWS server to expand the storage of your Linux computer. It also allows you to directly use the storage devices of the existing Windows server for Linux Server. With IP SAN solution provided by iStorage Server, you may install application and server software, as well as store data required wish you like. If you want to learn more about iStorage Server support for iSCSI under Linux operating system, please refer to this White Paper.
You can download Trial version of iStorage Server here.
 iStorage Server supports creating an iSCSI SAN for Windows Server 2008 clustering iSCSI, an Internet Protocol (IP)-based storage networking standard for linking data storage facilities. By carrying SCSI commands over IP networks, iSCSI is used to facilitate data transfers over intranets and to manage storage over long distances. iSCSI can be used to transmit data over local area networks (LANs), wide area networks (WANs), or the Internet and can enable location-independent data storage and retrieval. It is a popular Storage Area Network (SAN) protocol, allowing organizations to consolidate storage into data center storage arrays while providing hosts (such as database and web servers) with the illusion of locally-attached disks. Unlike traditional Fibre Channel, which requires special-purpose cabling, iSCSI can be run over long distances using existing network infrastructure. - Main benefits of using iSCSI SAN are:
- iSCSI can be run over long distances using existing network infrastructure.
- Simplified and consolidated storage management
- Easier virtualization
If you want to learn more about iStorage Server iSCSI SAN technology, and how to use it in Windows Server 2008, please refer to this White Paper.
You can download Trial version of iStorage Server here.
 iStorage Server supports creating a High-Availability iSCSI SAN for Citrix Xen Server Citrix Xen Server™ is the only enterprise-class, cloud-proven virtualization platform that delivers the critical features of live migration and centralized multi-server management at no cost. Xen Server is an open and powerful server virtualization solution that radically reduces datacenter costs by transforming static and complex datacenter environments into more dynamic, easy to manage IT service delivery centers. High availability is the implementation of technology so that if a component fails, another can take over for it. By using highly available platforms, the downtime for a system can be reduced, and, in many cases, it can be reduced to a short enough time that the users of the system do not see the failure. If you want to learn more about iStorage Server HA iSCSI SAN technology for Citrix Xen Server, and how to use it, please refer to this White Paper.
You can download Trial version of iStorage Server here.
 iStorage Server supports iSCSI SAN on Itanium Server KernSafe iStorage Server as first software fully supports Itanium architecture for creating iSCSI SAN Targets. The Itanium architecture is based on explicit instruction-level parallelism, in which decisions about which instructions to execute in parallel must be made by the compiler. This contrasts with other superscalar architectures which depend upon processor functionality that keeps track of instruction dependencies at runtime. Itanium cores up to and including Tukwila execute up to six instructions per clock cycle. Main benefits of Itanium architecture are: - Multi-OS support
- Lower overall Cost of Ownership for enterprise IT
- ·Assurance of leading performance and scalability over the long-term
- Greater memory addressability
- More complex applications and computing environments
- Secure web server transactions
- Computer aided design such as Mechanical Analysis
- Very large memory databases
- Industry-standard servers in every tier of the data center
KernSafe iStorage Server is an advanced and powerful, full-featured iSCSI Target software that makes any x86, x64 or even Itanium Windows machine into an iSCSI Target. iStorage Server is an IP SAN solution that allows you quickly export existing storages such disk images, physical disks, partitions, CD/DVD-ROMs, tapes or any other type of SCSI based devices and even a variety of popular CD/DVD images to its client machines, which delivers immediate benefits allowing storage to be consolidated, virtualized and centrally managed. iStorage Server also provides RAID-1 (mirror) feature, which allows you create two devices for mirror backup, the mirror devices can be local image files or remote iSCSI devices. iStorage Server has been added support for Microsoft Virtual Disk File (VHD) and VHD snapshots at the recent release. So it is an ideal choice for any sized business.
You can download Itanium native Trial version of iStorage Server here.
 iStorage Server supports creation of Failover ClusteringCluster Shared Volumes (CSV) is a feature of Failover Clustering available in Windows Server 2008 R2 for use with the Hyper-V role. A Cluster Shared Volume is a standard Cluster disk containing an NTFS volume that is made accessible for read and write operations by all nodes within the cluster. This gives the virtual machine (VM) complete mobility throughout the cluster as any node can be an owner, and changing owners is easy. In Windows Server 2008, the VM and all dependent LUN resources form a dependent group that can only be moved or failed over as a complete unit. This means that if additional VMs created dependencies on these same LUNs they become members of that same group and cannot be independently moved. Move one VM or LUN and you end up moving all of the VMs and LUNs in the group. Additionally, this model created storage management challenges where hundreds of VMs would require hundreds of LUNs. This all changes in Windows 2008 R2 with CSV. Now, the VMs with VHDs deployed on a single CSV have no dependency on the disk resource and can be freely moved to or from any node in the cluster. To understand how Cluster Shared Volumes (CSV) works in a failover cluster, it is helpful to review how a cluster works without CSV. Without CSV, a failover cluster allows a given disk (LUN) to be accessed by only one node at a time. Given this constraint, each Hyper-V virtual machine in the failover cluster requires its own set of LUNs in order to be migrated or fail over independently of other virtual machines. In this type of deployment, the number of LUNs must increase with the addition of each virtual machine, which makes management of LUNs and clustered virtual machines more complex. Cluster Shared Volumes provides the following benefits in a failover cluster: - The configuration of clustered virtual machines is much simpler than before.
- You can reduce the number of LUNs (disks) required for your virtual machines, instead of having to manage one LUN per virtual machine, which was previously the recommended configuration (because the LUN was the unit of failover). Many virtual machines can use a single LUN and can fail over without causing the other virtual machines on the same LUN to also fail over.
- You can make better use of disk space, because you do not need to place each Virtual Hard Disk (VHD) file on a separate disk with extra free space set aside just for that VHD file. Instead, the free space on a Cluster Shared Volume can be used by any VHD file on that volume.
- You can more easily track the paths to VHD files and other files used by virtual machines. You can specify the path names, instead of identifying disks by drive letters (limited to the number of letters in the alphabet) or identifiers called GUIDs (which are hard to use and remember). With Cluster Shared Volumes, the path appears to be on the system drive of the node, under the \ClusterStorage folder. However, this path is the same when viewed from any node in the cluster.
- If you use a few Cluster Shared Volumes to create a configuration that supports many clustered virtual machines, you can perform validation more quickly than you could with a configuration that uses many LUNs to support many clustered virtual machines. With fewer LUNs, validation runs more quickly. (You perform validation by running the Validate a Configuration Wizard in the snap-in for failover clusters.)
- There are no special hardware requirements beyond what is already required for storage in a failover cluster (although Cluster Shared Volumes require NTFS).
- Resiliency is increased, because the cluster can respond correctly even if connectivity between one node and the SAN is interrupted, or part of a network is down. The cluster will re-route the Cluster Shared Volumes communication through an intact part of the SAN or network.
On more information on how to deploy CSV in Windows Server 2008 R2, please refer to this site http://blogs.msdn.com/b/clustering/archive/2009/02/19/9433146.aspx
You can download Trial version of iStorage Server here.
|











 RSS Feed
RSS Feed